What is a Network Security Key and How Can You Find Yours?
date
Mar 11, 2022
slug
what-is-a-network-security-key
status
Published
summary
When defending your home network from invaders, knowing security terminology helps. While the definition of network security key is in the context (a key that secures your network), it comes in many forms. Below, we will provide more information on everything you need to know about a network security key.
tags
Website
type
Post
featured_image_url
Author
Berktug Mutlu
category
Privacy & Security
meta_title
What is a Network Security Key and How Can You Find Yours? - FastVPN
When defending your home network from invaders, knowing security terminology helps. While the definition of network security key is in the context (a key that secures your network), it comes in many forms. Below, we will provide more information on everything you need to know about a network security key.
What is a Network Security Key?Is The Network Security Key The Same As Your Password?How To Change Your Network Security KeyHow Can You Find a Network Security Key? (On Any Platform)On Your RouterOn Windows 10 or 11On Mac DevicesOn iOS Devices (iPhones)On Android DevicesDifferent Types of Network Security KeysWEP (Wired Equivalent Privacy)WPA/WPA2/WPA3 (WiFi Protected Access)Two-Factor Authentication KeysWhat are the Benefits of Network Security KeysTips for Creating a Strong WiFi PasswordConclusion – Final Network Security Tips
What is a Network Security Key?
A network security key, or WiFi password, is a specific code that people need to access your network. In an ideal home internet setup, you would require a network password (key) to access the internet.
All wireless devices need a key if your home internet security is set up correctly. What that key looks like differs depending on your chosen security protocol, a topic we will revisit later.
These keys are limited to wireless networks. However, wired connections might have network limitations locked behind similar keys, but these are not the same kinds of keys.
A standard WiFI password does not provide you with admin privileges. For example, you’ll need the router’s admin password if you want to change network settings (which differs from the WiFi passcode). So a network security key grants access to the network but doesn’t provide access to change router settings.
Is The Network Security Key The Same As Your Password?
Your network key is the same thing as your WiFi password. There is never a case where this is untrue, as the term WiFi password and security key are interchangeable when used in this context.
The default security key (what your router initially comes with) might differ from what you have it set to now. Often, you set these up with your Internet Service Provider (ISP).
ISPs typically won’t help you in cases where you have a third-party router. This is because their network technicians don’t have built-in remote access from company-specific routers. So they can’t walk you through setting up a key because they don’t have access.
How To Change Your Network Security Key
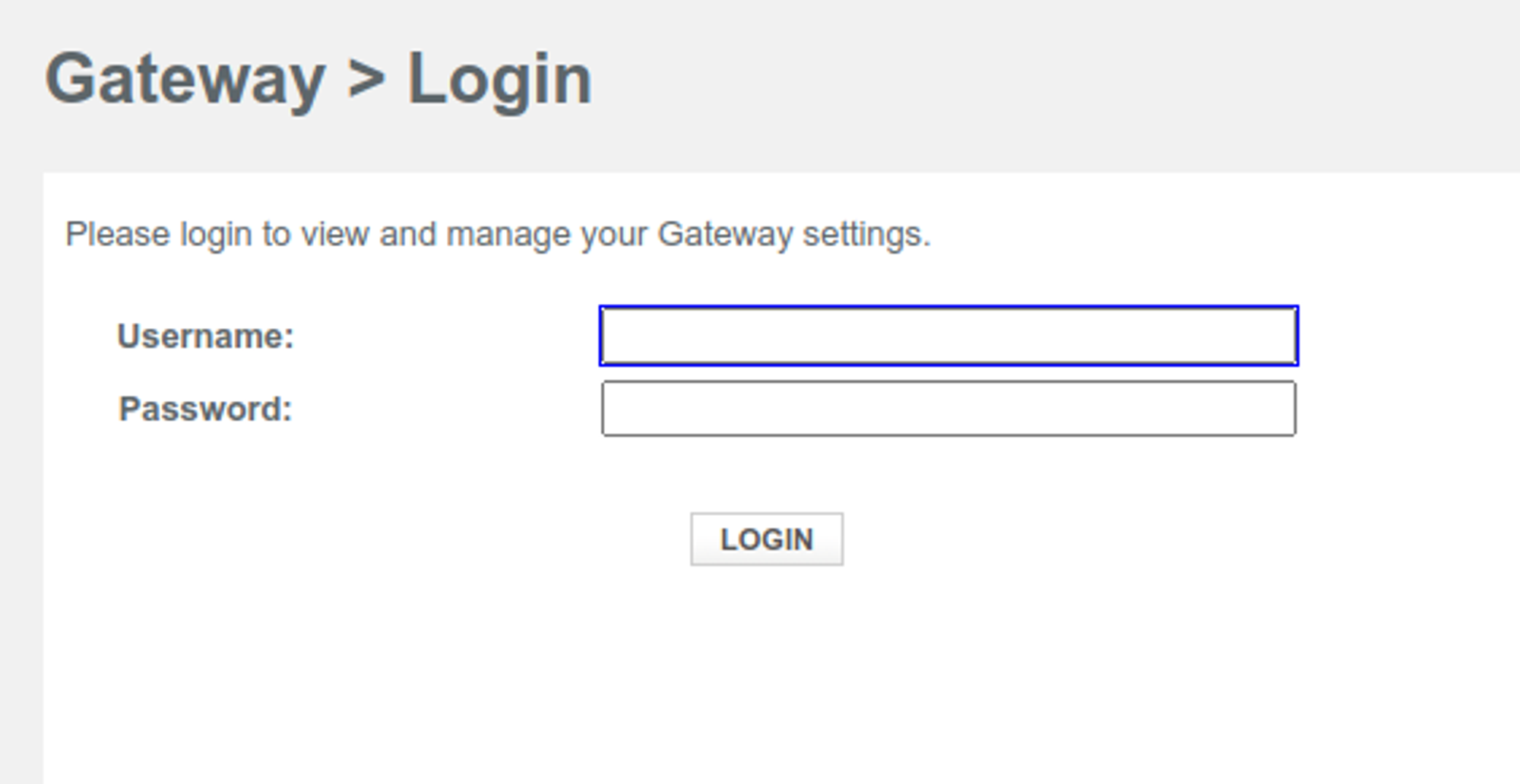
In cases where your ISP won’t show you how to establish a key, you can use these steps to select your wireless password:
- Access your router through your default gateway (you can find this gateway on the side of your router or from your computers network settings page)
- Put your default gateway IP in your browser’s address bar
- Insert your admin credentials (username and password). You can find these on the side of your router or in your owner’s manual.
- Access your router’s basic settings
- Choose your security type (read below for more details).
- Insert your password (Choose WPA2 for something 100% custom)
- Save the details
What you change your security key into varies depending on the type of security you choose. Selecting a strong password is essential, and you can read some tips on that below.
How Can You Find a Network Security Key? (On Any Platform)
In cases where you want to share your password with a trusted friend, you need to know where to find it. Here are your different options:
On Your Router
Finding the network key on your router can be done in one of two ways:
- For routers fresh from the factory, you can find it on the side of your router or in your owner’s manual
- Otherwise, you can follow the steps for changing your password above and check the “view password” button
Most routers enable you to view your password by clicking a check box above or below that reveals your password. If your router doesn’t have this, you might change your password to something you can remember.
On Windows 10 or 11
Viewing your password on any connected device can be done through the internet settings. Windows devices must follow the following:
- Go to “settings.”
- Select “Network & Internet” within your control panel
- Select the internet you are connected to
- Choose “properties”
- Check the box next to “show characters.”
Your other option is to select the network from your taskbar. Selecting properties will also reveal a menu to show your internet password.
On Mac Devices
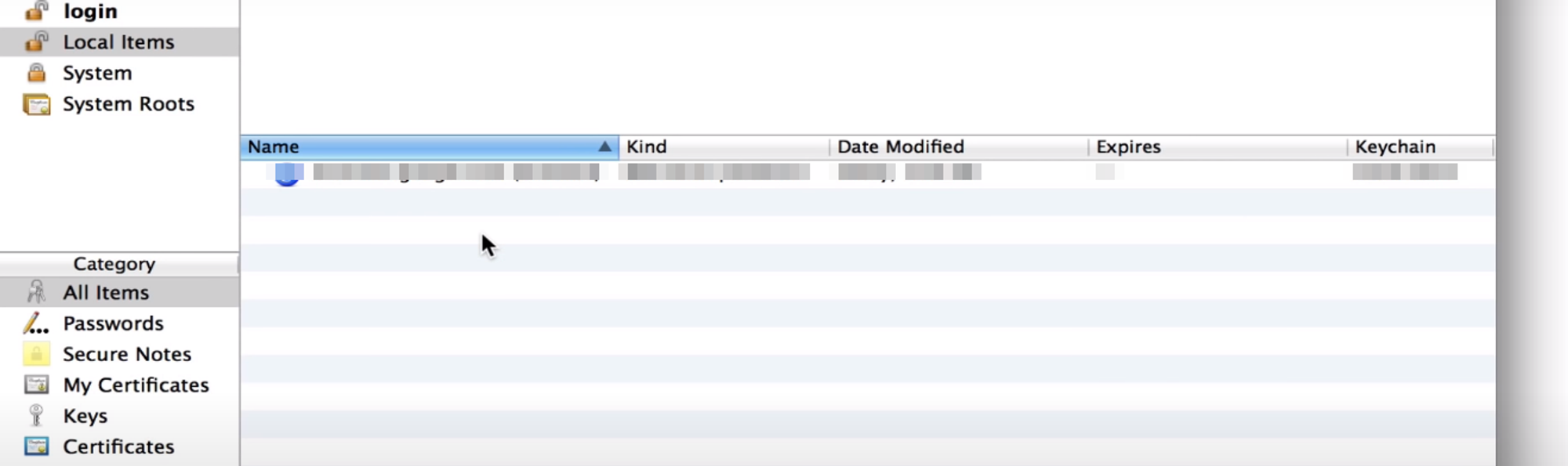
If you are on macOS, you can follow these steps to find your password:
- Go to “keychain access” in the upper-right corner
- Select “passwords” under “system.”
- Find the name of your wireless network and double click it
- Select “show password.” and insert your computer’s username and password
- Click “view and show” password
Keychain Access is Mac’s password manager, so you can store all of your network credentials here. The use of a password manager can be great, but I wouldn’t recommend Apple’s manager.
On iOS Devices (iPhones)
Like Mac devices, iOS enables you to look up the wireless password through the network settings. To do so, all you need to do is access network settings.
Your other option is to share the WiFi password via a personal hotspot. You can check that out through this video:
On Android Devices
Like other mobile devices, Google’s Android enables you to share a wireless connection through hotspot access. However, this hotspot cannot be an extension of your WiFi, only an extension of your mobile network.
Mobile networks often require you to pay extra for establishing wireless hotspots. The downer about this is that you can only “share your WiFI password” from Android devices by typing them in from another source.
Different Types of Network Security Keys
Most modern routers rely on one of two types of security keys:
- WEP (the older key)
- WPA or WPA2 (the newer key)
Some networks also require different types of authentication, which we will address below. All WiFi protocols come from the same source: the WiFi Alliance.
WEP (Wired Equivalent Privacy)
WEP, or Wired Equivalent Privacy, is the earliest known element of wireless protection. It is an old-fashioned method of security known for 64-bit 128-bit key encryption methods.
Those who read our basics blog on VPNs know that this encryption style is not secure. As a result, WEP was no longer supported as of 2004.
WEP persists in a small number of households with outdated tech. To address this weakness, WEP made way for WPA.
WPA/WPA2/WPA3 (WiFi Protected Access)
WPA, or WiFi Protected Access, was released a year before (2003) the discontinuation of WEP. WPA was the earliest form using a more modern 256-bit encryption set.
When people refer to a WPA key, they talk about the wireless network key. This makes it another term interchangeable with wireless passwords.
WPA2 (still often called just WPA) was geared more towards offering shared passcodes. This is where WPA2-PSK comes from, as PSK standards for Pre-Shared Passcodes.
WPA2 also included two additional well-known encryption algorithms:
- AES (Advanced Encryption Standard)
- CCMP (Counter Mode Cipher Block Chaining Message Authentication Protocol)
Both were advancing the original WPA’s TKP (Temporal Key Integrity). Eventually, an additional upgrade was found in WPA3, released in 2018, making it a 14-year gap from WPA2 (in 2004).
WPA3 is known to offer further protection through the following bonuses:
- Usage of 256-bit encryption keys
- Use of a DPP (Device Provisioning Protocol) for near field communication of data through QR codes or NFC tags
- Support for Extensible Authentication Protocol (EAP)
- Requires connections through a process (not a one-use password)
Despite the enhanced security, WPA3 is known for having numerous vulnerabilities. In 2019, security researchers revealed these exploits:
- Downgrade attacks can convince WPA3 networks to rely on less secure password systems.
- Side-channel information leak attacks can trick devices into relying on weaker algorithms that leak information.
- Denial of service attack vulnerabilities enables hackers to crash the security system.
The WiFi Alliance announced bug fixes to bot issues. Regardless, these vulnerabilities are typical with the release of these widespread security platforms.
Two-Factor Authentication Keys
On the business side of confirmation, two-factor authentication is an aspect of network access. Two-factor authentication (2FA) involves verifying your identity with your network password and other signatures.
Multi-factor authentication (MFA, another word for it) makes it possible to limit network access by specific identities. This can be important in cases where you want to take extra steps to prevent unauthorized access.
MFA comes in many forms:
- Using a physical authentication tool
- Sending a code to your smartphone via text, call, or app
- Verifying your identity using biometric data (fingerprints)
Because MFA requires access to multiple devices and means of verification, it is the ultimate way to prevent unwanted access. The problem is that you’ll have to put personal identification on some third-party sites to get this done. For example, some privacy-conscious individuals might not want to use Google Authenticator.
What are the Benefits of Network Security Keys
- Protect your home or office network. Despite security vulnerabilities, a good password is a secure connection. Having one way provides your network with security.
- Identifies attempts at evil twin attacks. These attacks happen when someone tries to fool local users into thinking they are the available network. This often occurs with public networks, so establishing a WiFi password and posting it in your business can prevent people from being fooled.
- Prevent hackers from stealing your information. When hackers get access to your home network, they either piggyback (steal your bandwidth and slow your connections) or hijack (steal files on a shared home network).
Tips for Creating a Strong WiFi Password
- Avoid social security numbers.
- Don’t use addresses, pet names, or anything you share with the public.
- Use a random combination of characters and numbers
- Random phrases might also work
- Random capitalization also helps
- Do not reuse passwords from other sources
Conclusion – Final Network Security Tips
You might wonder why you should bother with a network security key if known exploits for all types of security keys. The reality is that if you don’t share your network publically, most home networks can avoid many risks. Business networks might consider adding multi-factor authentication for additional security. Guest networks (like your public cafes) should be sure to set up a dual network (one only for employees and one for visitors).
For additional non-network security, download The Fast VPN. A VPN ensures that you aren’t releasing essential data to anyone who doesn’t need to know.